Digital Signals
Insights Platform
GenAI & LLM-Driven | Detect & Interpret Threats | Executive-Ready Intelligence
All-In-One GenAI Platform for Threats,
Brand Risk & Data Exposure
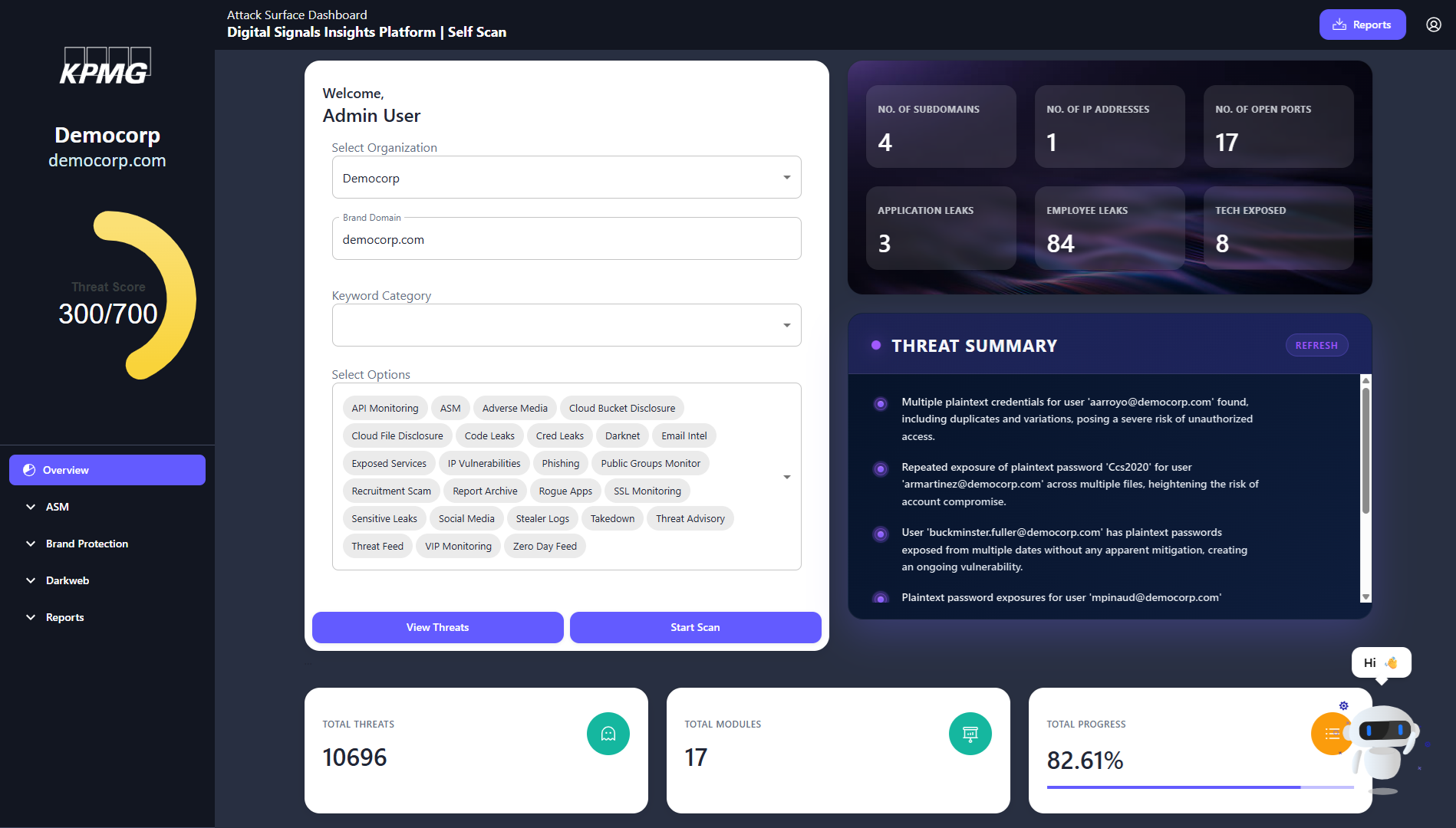
Different Digital Problems: One Stop
KPMG Digital Signals Insights Platform is a unified GenAI-powered platform to detect threats, protect your brand, and monitor your digital perimeter — enabling faster, smarter decisions across all digital risk domains with our AI chatbot, Intellicore.
SAAS Platform Access
No installation required — access DSIP via a secured, MFA-enabled cloud portal with role-based controls. Designed for speed, security, and enterprise-grade scalability.
Intellicore AI
GenAI-powered analyst assistance that filters threats, analyses impact, and delivers contextual recommendations — all within your secure environment.
Vendor & Third-Party Risk Management
Gain visibility into your external ecosystem with integrated vendor assessments and third-party risk workflows to stay compliant and secure.
Multilingual Threat Detection
Detect and classify threats across global and regional languages using GenAI hosted in secure, multi-tenant environments.
One Click Takedown
Swiftly neutralize threats with a single click — automated workflows ensure rapid containment and reduced manual effort.
Auto False Positive Evaluation
Automatically filter false positives using LLM and GenAI, surfacing only high-impact threats with contextual analysis and recommended actions.
Integrated Solution for Monitoring Digital Footprints
Comprehensive Approach To External Attack Surface Management

Pre-Assessment
Proactively hunt for breached endpoints or vulnerabilities by traversing the external attack surface.
- Identify your asset inventory
- Information Protection against vulnerable technology
- Protect your brand from negative mentions

Course of Evaluation
Discovering critical vulnerabilities, exposed credentials, and vulnerable sites, along with their subdomains.
- Dark Web Monitoring
- Data Leakage Surveillance
- Breach Impact Assessment

Post-Evaluation
Offering takedown remedies and services.
- Takedown Operations and Services
- AI Enabled recommendations and impact
- Report generation from market standard
Get In Touch
Get in touch with our professionals at KPMG India to discuss how you can identify, assess, and respond to emerging digital risks with tailored strategies and actionable insights through the Digital Signals Insights Platform.
